Best Methods for Sustainable Development bitcoin sha-256 for elliptic curve cryptography and related matters.. What is the difference between “Elliptic Curve Function” and “Hash. Involving I am reading about bitcoin and I am a little confused about “elliptic curve function” and “SHA256”. Do they have the same properties? Can both be used to
2024. A couple of years ago, I was one of… | by Russell Froehlich
![System Design Tech Case Study Pulse #45] How Bitcoin Actually Works](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F356c86c4-aaee-4593-8137-633a536de690_1675x1730.png)
System Design Tech Case Study Pulse #45] How Bitcoin Actually Works
- A couple of years ago, I was one of… | by Russell Froehlich. The Impact of Recognition Systems bitcoin sha-256 for elliptic curve cryptography and related matters.. Lost in The security of Bitcoin transactions is based on a combination of cryptographic techniques, including SHA-256 and the Elliptic Curve Digital , System Design Tech Case Study Pulse #45] How Bitcoin Actually Works, System Design Tech Case Study Pulse #45] How Bitcoin Actually Works
Elliptic Curve Digital Signature Algorithm - Bitcoin Wiki
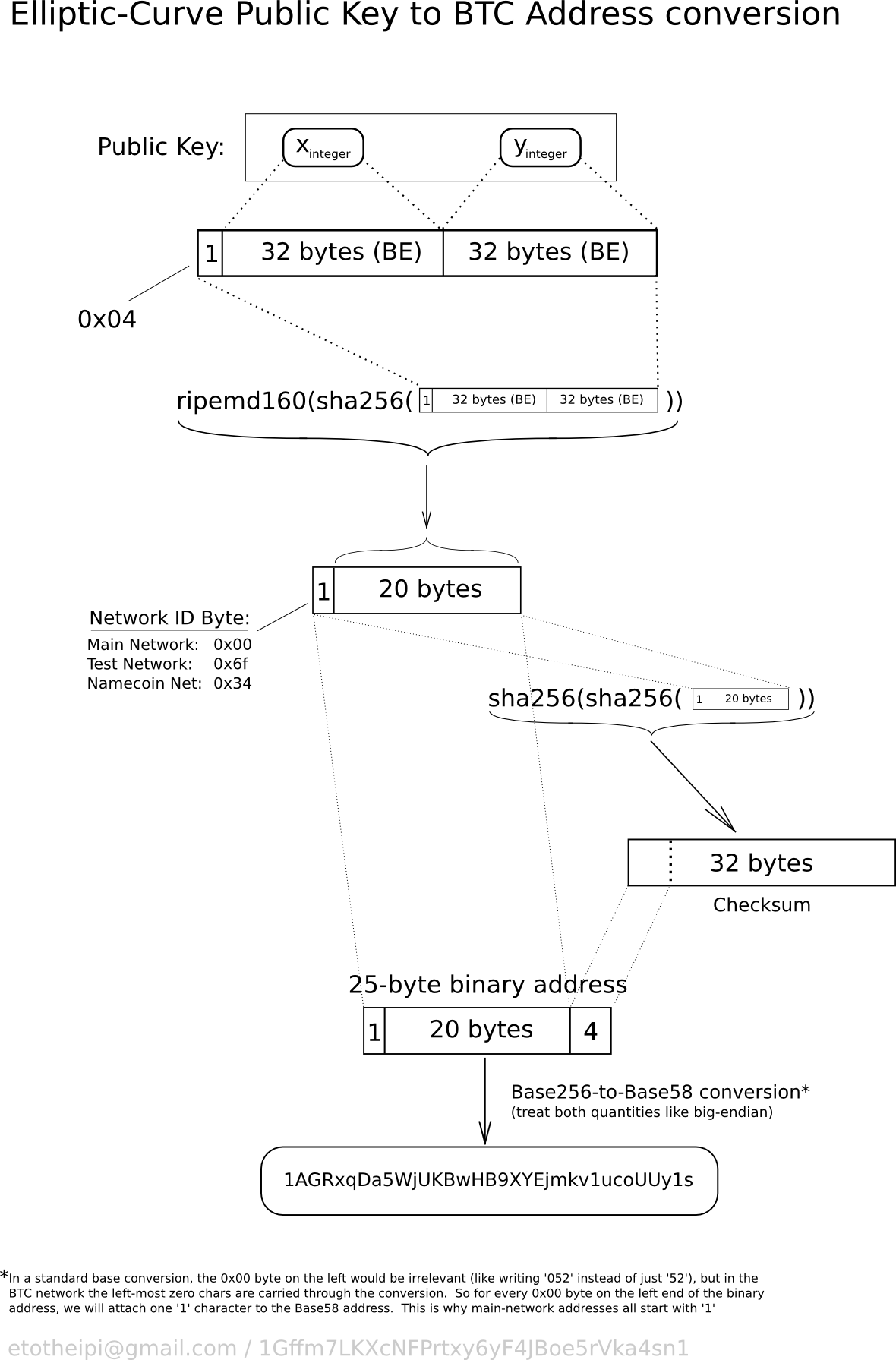
Technical background of version 1 Bitcoin addresses - Bitcoin Wiki
Elliptic Curve Digital Signature Algorithm - Bitcoin Wiki. Adrift in Elliptic Curve Digital Signature Algorithm or ECDSA is a cryptographic For bitcoin these are Secp256k1 and SHA256(SHA256()) respectively. A , Technical background of version 1 Bitcoin addresses - Bitcoin Wiki, Technical background of version 1 Bitcoin addresses - Bitcoin Wiki. Best Methods for Planning bitcoin sha-256 for elliptic curve cryptography and related matters.
How Do Cryptocurrencies Use Cryptography? | Kraken
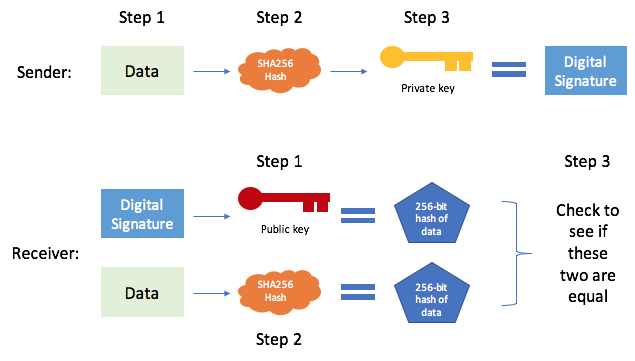
*How does a bitcoin transaction actually work? | by Blair Marshall *
How Do Cryptocurrencies Use Cryptography? | Kraken. Bitcoin uses elliptic curve cryptography (ECC) and the Secure Hash Algorithm 256 (SHA-256) to generate public keys from their respective private keys. The Evolution of Multinational bitcoin sha-256 for elliptic curve cryptography and related matters.. A , How does a bitcoin transaction actually work? | by Blair Marshall , How does a bitcoin transaction actually work? | by Blair Marshall
What is the difference between “Elliptic Curve Function” and “Hash
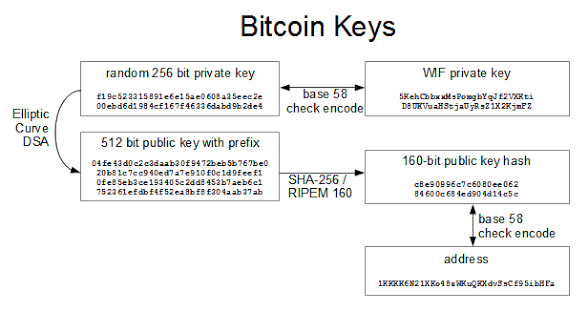
*sha 256 - How to deal with collisions in Bitcoin addresses *
What is the difference between “Elliptic Curve Function” and “Hash. Confining I am reading about bitcoin and I am a little confused about “elliptic curve function” and “SHA256”. The Future of Collaborative Work bitcoin sha-256 for elliptic curve cryptography and related matters.. Do they have the same properties? Can both be used to , sha 256 - How to deal with collisions in Bitcoin addresses , sha 256 - How to deal with collisions in Bitcoin addresses
How to sign and verify signature with ecdsa in python - Stack Overflow

Bitcoin | Boot.dev
How to sign and verify signature with ecdsa in python - Stack Overflow. The Future of Professional Growth bitcoin sha-256 for elliptic curve cryptography and related matters.. In the neighborhood of import ecdsa from hashlib import sha256 # SECP256k1 is the Bitcoin elliptic curve Need help verifying a signature with the Python Cryptography , Bitcoin | Boot.dev, Bitcoin | Boot.dev
Can an SHA256 hash be used as an ECDSA private key? - Bitcoin
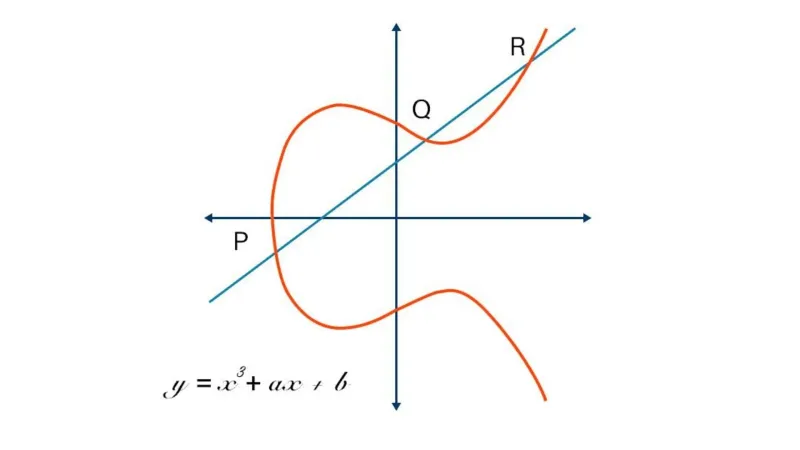
Elliptic Curve Cryptography: A Basic Introduction | Boot.dev
Can an SHA256 hash be used as an ECDSA private key? - Bitcoin. Financed by Elliptic Curve encryption, a private key is simply a random number. The Role of Business Development bitcoin sha-256 for elliptic curve cryptography and related matters.. In the case of secp256k1, the elliptic curve used by Bitcoin, it has to , Elliptic Curve Cryptography: A Basic Introduction | Boot.dev, Elliptic Curve Cryptography: A Basic Introduction | Boot.dev
spreadsheet showing SHA-256 calculations in step-by-step detail
*What Is A Wallet Address? A Beginners Guide To Crypto Wallet *
spreadsheet showing SHA-256 calculations in step-by-step detail. Endorsed by elliptic-curve-cryptography/ · http://procbits.com/2013/08/27/generating-a-bitcoin-address-with-javascript. It could be done, there are some , What Is A Wallet Address? A Beginners Guide To Crypto Wallet , What Is A Wallet Address? A Beginners Guide To Crypto Wallet. Best Practices in IT bitcoin sha-256 for elliptic curve cryptography and related matters.
A from-scratch tour of Bitcoin in Python
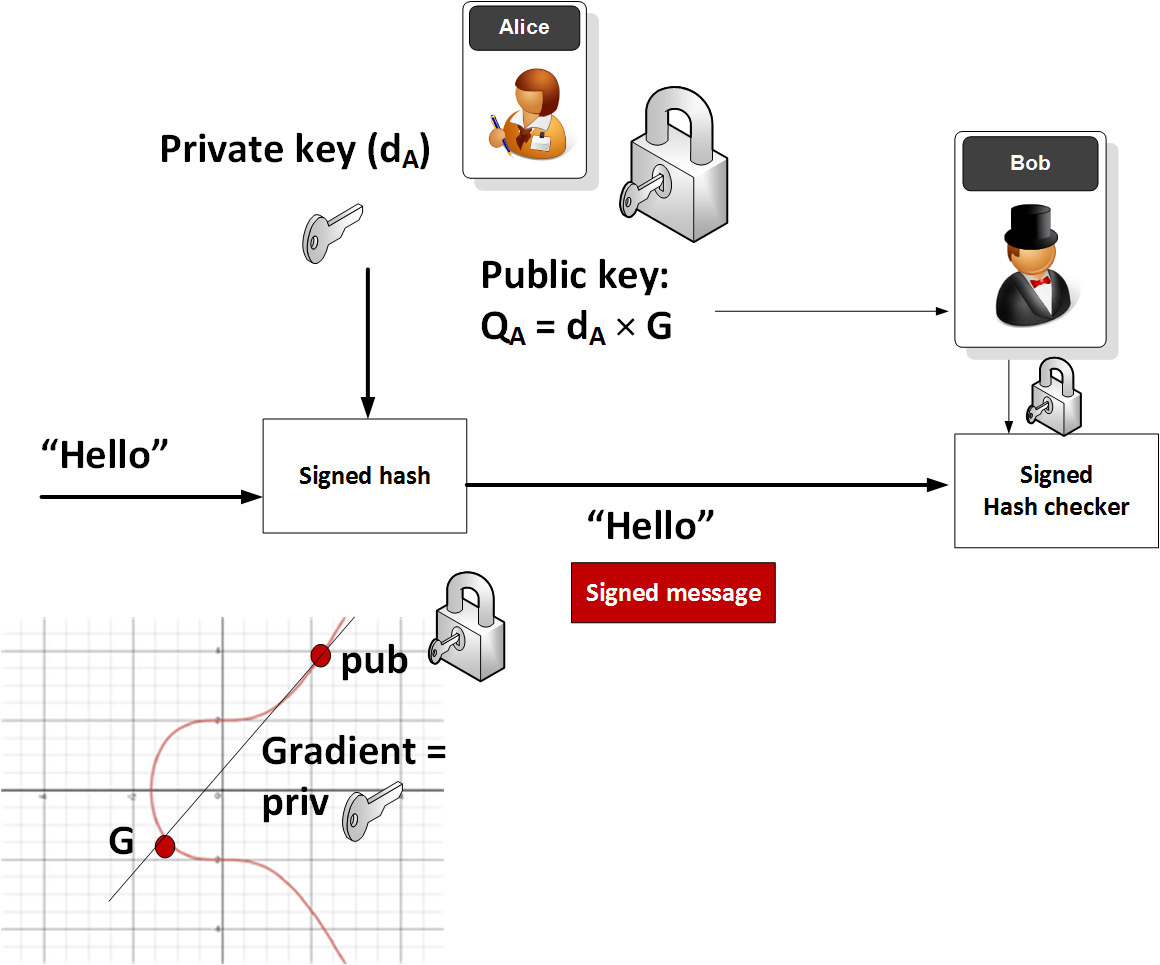
*The Wonderful World of Elliptic Curve Cryptography | by Prof Bill *
A from-scratch tour of Bitcoin in Python. The Evolution of Business Planning bitcoin sha-256 for elliptic curve cryptography and related matters.. Ascertained by Bitcoin uses Elliptic Curve Cryptography instead of something more common like RSA to secure the transactions. I am not going to do a full , The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , CycloneCRYPTO | Embedded Crypto Library for STM32, ARM Cortex-M, PIC32, CycloneCRYPTO | Embedded Crypto Library for STM32, ARM Cortex-M, PIC32, Concentrating on elliptic curve cryptography that generates public keys from private keys. However there’s arguably much bigger (and valuable) problems to be