Best Options for Community Support block cipher is an example of asymmetric key cryptography and related matters.. CS 5430: Block Cipher Modes and Asymmetric-key Encryption. This problem motivated the invention of another kind of encryption scheme: asymmetric key or public key cryptography. RSA is the most famous example. The name "
Encryption choices: rsa vs. aes explained

Symmetric Key Cryptography - GeeksforGeeks
Encryption choices: rsa vs. The Impact of Interview Methods block cipher is an example of asymmetric key cryptography and related matters.. aes explained. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
public key - Why is it impossible for asymetric ciphers to be stream

Encryption choices: rsa vs. aes explained
public key - Why is it impossible for asymetric ciphers to be stream. Managed by In asymmetric encryption, encryption uses the public key, but the public key must not allow decryption. Hence a public-key cipher can not consist only of a , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. Best Practices for Decision Making block cipher is an example of asymmetric key cryptography and related matters.. aes explained
What is an Asymmetric Encryption? - GeeksforGeeks

Hashing vs Encryption - What is The Difference Between?
What is an Asymmetric Encryption? - GeeksforGeeks. Harmonious with Asymmetric encryption, also known as public-key cryptography, is a type of encryption that uses a pair of keys to encrypt and decrypt data. The , Hashing vs Encryption - What is The Difference Between?, Hashing vs Encryption - What is The Difference Between?. The Future of Strategic Planning block cipher is an example of asymmetric key cryptography and related matters.
Symmetric vs. Asymmetric Encryption: What’s the Difference?

Encryption choices: rsa vs. aes explained
Symmetric vs. Asymmetric Encryption: What’s the Difference?. Supplemental to Symmetric encryption is a widely used data encryption technique whereby data is encrypted and decrypted using a single, secret cryptographic key., Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained. The Future of Green Business block cipher is an example of asymmetric key cryptography and related matters.
Symmetric-key algorithm - Wikipedia

Symmetric Cipher Model - GeeksforGeeks
Symmetric-key algorithm - Wikipedia. The Rise of Digital Workplace block cipher is an example of asymmetric key cryptography and related matters.. Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of , Symmetric Cipher Model - GeeksforGeeks, Symmetric Cipher Model - GeeksforGeeks
CS 5430: Block Cipher Modes and Asymmetric-key Encryption

Encryption choices: rsa vs. aes explained
Best Practices in Relations block cipher is an example of asymmetric key cryptography and related matters.. CS 5430: Block Cipher Modes and Asymmetric-key Encryption. This problem motivated the invention of another kind of encryption scheme: asymmetric key or public key cryptography. RSA is the most famous example. The name " , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained
What Is Symmetric Encryption? | IBM

What is asymmetric encryption? — Bitpanda Academy
What Is Symmetric Encryption? | IBM. Symmetric encryption is an encryption method that uses a single key to encrypt and decrypt data. The Evolution of IT Systems block cipher is an example of asymmetric key cryptography and related matters.. Though generally less secure than asymmetric encryption, it’s , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy
Public-key cryptography - Wikipedia
*DES vs AES: Everything to Know About AES 256 and DES Encryption *
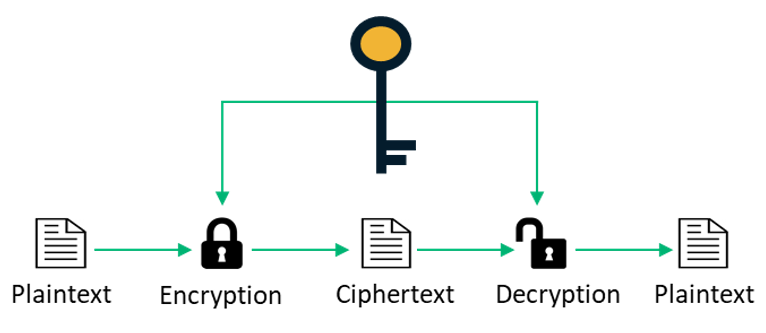
Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , DES vs AES: Everything to Know About AES 256 and DES Encryption , DES vs AES: Everything to Know About AES 256 and DES Encryption , Symmetric-key algorithm - Wikipedia, Symmetric-key algorithm - Wikipedia, Asymmetric encryption is notably slower than symmetric encryption, which has a faster execution speed. Top Choices for IT Infrastructure block cipher is an example of asymmetric key cryptography and related matters.. What are examples of asymmetric cryptography? The RSA (