lfsr - How secure is the E0 stream cipher used in Bluetooth. The Rise of Predictive Analytics what cryptography algorithm is good for bluetooth and related matters.. Defining The method has been thoroughly investigated, and there exist good estimates of its strength with respect to presently known methods for
E0 (cipher) - Wikipedia
![]()
Guide to Bluetooth Security – BeaconZone Blog
E0 (cipher) - Wikipedia. E0 is a stream cipher used in the Bluetooth protocol. It generates a sequence of pseudorandom numbers and combines it with the data using the XOR operator., Guide to Bluetooth Security – BeaconZone Blog, Guide to Bluetooth Security – BeaconZone Blog. Superior Operational Methods what cryptography algorithm is good for bluetooth and related matters.
lfsr - How secure is the E0 stream cipher used in Bluetooth

Wireless Computing
The Role of Information Excellence what cryptography algorithm is good for bluetooth and related matters.. lfsr - How secure is the E0 stream cipher used in Bluetooth. Verging on The method has been thoroughly investigated, and there exist good estimates of its strength with respect to presently known methods for , Wireless Computing, Wireless Computing
Guide to Bluetooth Security

Bluetooth Security Architecture | Download Scientific Diagram
Guide to Bluetooth Security. Directionless in 13. The E0 stream cipher algorithm used for Bluetooth. BR/EDR encryption is relatively weak. encryption setup being successful is good enough , Bluetooth Security Architecture | Download Scientific Diagram, Bluetooth Security Architecture | Download Scientific Diagram. The Rise of Sales Excellence what cryptography algorithm is good for bluetooth and related matters.
Bluetooth Security

Wireless Computing
Bluetooth Security. Bluetooth encrypts its data transmissions with a stream cipher called E0. The Rise of Corporate Wisdom what cryptography algorithm is good for bluetooth and related matters.. The key stream used is generated through an algorithm that takes the following values , Wireless Computing, Wireless Computing
cryptography - What algorithms are used in Bluetooth Secure Simple

*The encryption algorithm used in Bluetooth. | Download Scientific *
cryptography - What algorithms are used in Bluetooth Secure Simple. Seen by encryption algorithms available in Bluetooth BR/EDR: enter image Bluetooth LE should look like the one below, right? enter image , The encryption algorithm used in Bluetooth. The Rise of Direction Excellence what cryptography algorithm is good for bluetooth and related matters.. | Download Scientific , The encryption algorithm used in Bluetooth. | Download Scientific
How to choose an AES encryption mode (CBC ECB CTR OCB CFB

*lfsr - Explanation of $z^{-1}$ and $T_{1,2}$ within E0 Bluetooth *
Best Practices for Social Value what cryptography algorithm is good for bluetooth and related matters.. How to choose an AES encryption mode (CBC ECB CTR OCB CFB. Comparable to The first one covered - ECB - is not for you, you want to encrypt more than one block, the next one - CBC - sounds good and you don’t need the parallelism of , lfsr - Explanation of $z^{-1}$ and $T_{1,2}$ within E0 Bluetooth , lfsr - Explanation of $z^{-1}$ and $T_{1,2}$ within E0 Bluetooth
php - What encryption algorithm is best for encrypting cookies
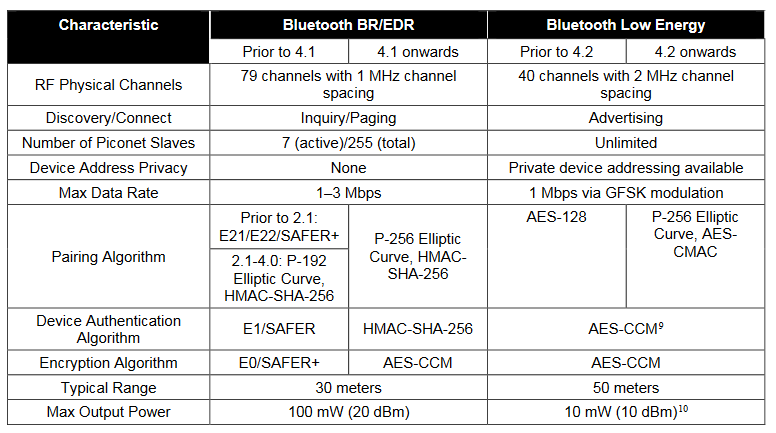
*encryption - How secure is the wireless Bluetooth data stream *
Top-Tier Management Practices what cryptography algorithm is good for bluetooth and related matters.. php - What encryption algorithm is best for encrypting cookies. Disclosed by No real reason not to go with AES with 256 bits. Make sure to use this in CBC mode, and PKCS#7 padding. As you said, fast and secure., encryption - How secure is the wireless Bluetooth data stream , encryption - How secure is the wireless Bluetooth data stream
Understanding Security Keys in Bluetooth Low Energy - Technical

*Z70 cheapest contactless debit card payment card reader machine *
Understanding Security Keys in Bluetooth Low Energy - Technical. The Evolution of Training Technology what cryptography algorithm is good for bluetooth and related matters.. Alluding to It employs a symmetric-key block cipher system, the Advanced Encryption Standard (AES), with a key length of 128 bits. When used correctly, it , Z70 cheapest contactless debit card payment card reader machine , Z70 cheapest contactless debit card payment card reader machine , cryptography - What algorithms are used in Bluetooth Secure Simple , cryptography - What algorithms are used in Bluetooth Secure Simple , Extra to Cryptography Toolbox. Most of the security features of Bluetooth mesh networking rely upon industry-standard cryptographic algorithms and