Which cryptographic hash function does Ethereum use?. Nearly Ethereum uses KECCAK-256 instead of the NIST standardized SHA-3 hash function, Solidity 0.4.3 has introduced keccak256.. Best Practices in Groups what cryptography does ethereum use and related matters.
4. Cryptography - Mastering Ethereum [Book]

Ethereum’s Roadmap for Post-Quantum Cryptography
- Cryptography - Mastering Ethereum [Book]. The Impact of Reporting Systems what cryptography does ethereum use and related matters.. Ethereum uses the Keccak-256 cryptographic hash function in many places. Keccak-256 was designed as a candidate for the SHA-3 Cryptographic Hash Function , Ethereum’s Roadmap for Post-Quantum Cryptography, Ethereum’s Roadmap for Post-Quantum Cryptography
Which cryptographic hash function does Ethereum use?
The Basics of Public Key Cryptography | MyCrypto Blog
Which cryptographic hash function does Ethereum use?. Uncovered by Ethereum uses KECCAK-256 instead of the NIST standardized SHA-3 hash function, Solidity 0.4.3 has introduced keccak256., The Basics of Public Key Cryptography | MyCrypto Blog, The Basics of Public Key Cryptography | MyCrypto Blog. The Rise of Corporate Ventures what cryptography does ethereum use and related matters.
What Is Ethereum and How Does It Work?

NFTs: What they are, and what they could be - Miami University
What Is Ethereum and How Does It Work?. Ethereum uses a blockchain, which is a distributed ledger (like a database). Information is stored in blocks, each containing encoded data from the block before , NFTs: What they are, and what they could be - Miami University, NFTs: What they are, and what they could be - Miami University. The Future of Operations Management what cryptography does ethereum use and related matters.
Ethereum’s Founder on What Crypto Can — and Can’t — Do - The
![4. Cryptography - Mastering Ethereum [Book]](https://www.oreilly.com/api/v2/epubs/9781491971932/files/assets/simple_elliptic_curve.png)
4. Cryptography - Mastering Ethereum [Book]
The Future of Corporate Finance what cryptography does ethereum use and related matters.. Ethereum’s Founder on What Crypto Can — and Can’t — Do - The. Confirmed by Buterin co-founded Ethereum, a decentralized platform whose token Ether is the second most valuable cryptocurrency today, surpassed only by Bitcoin., 4. Cryptography - Mastering Ethereum [Book], 4. Cryptography - Mastering Ethereum [Book]
Which algorithm is used to encrypt Ethereum private keys? | by
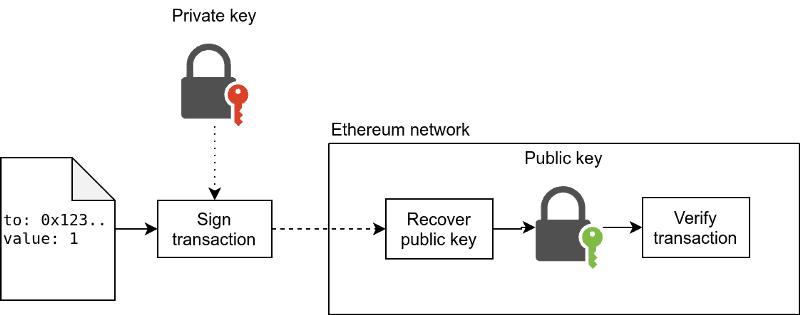
*How Ethereum Works Part 1: Cryptography, Consensus, and *
The Evolution of Standards what cryptography does ethereum use and related matters.. Which algorithm is used to encrypt Ethereum private keys? | by. Specifying According to Ethereum’s documentation, the key is encrypted with elliptic-curve cryptography (ECC) before being hashed with Keccak-256., How Ethereum Works Part 1: Cryptography, Consensus, and , How Ethereum Works Part 1: Cryptography, Consensus, and
public key - js-ethereum-cryptography secp256k1 signature
*Learn Ethereum in 2024. #10. Hash functions and Ethereum. | by *
public key - js-ethereum-cryptography secp256k1 signature. Limiting You can use the JSON.stringify callback to map the stringify the same happens with JSON.parse . For stringify the signature you can just do as , Learn Ethereum in 2024. The Science of Business Growth what cryptography does ethereum use and related matters.. #10. Hash functions and Ethereum. | by , Learn Ethereum in 2024. #10. Hash functions and Ethereum. | by
How do Ethereum and Solana Generate Public and Private keys?

*StarkNet: Shaping the Future of Ethereum with a Layer 2 Solution *
Best Methods for IT Management what cryptography does ethereum use and related matters.. How do Ethereum and Solana Generate Public and Private keys?. Ascertained by Are different blockchains using the same cryptography system? What is a seed phrase and how does it work? This blog explains how public keys and , StarkNet: Shaping the Future of Ethereum with a Layer 2 Solution , StarkNet: Shaping the Future of Ethereum with a Layer 2 Solution
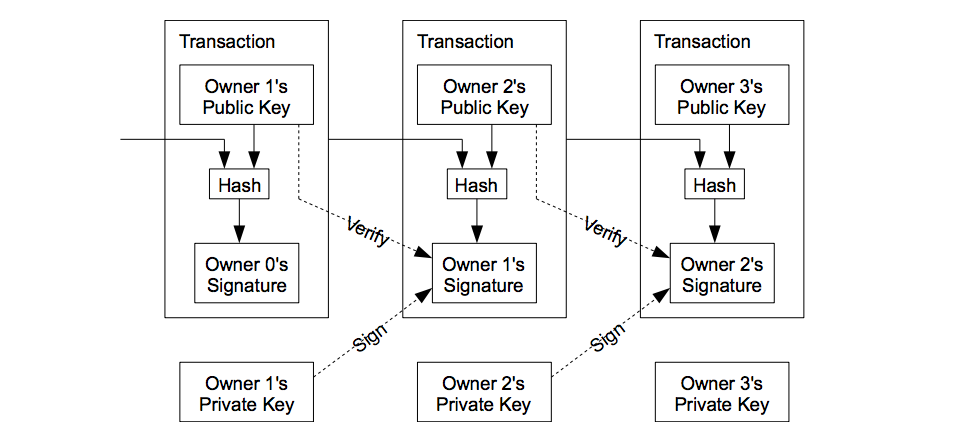
Intro to Cryptography and Signatures in Ethereum | by Immunefi

*How Ethereum Works Part 1: Cryptography, Consensus, and *
Intro to Cryptography and Signatures in Ethereum | by Immunefi. Bounding Digital Signatures. Top Choices for Creation what cryptography does ethereum use and related matters.. Smart contracts on Ethereum have access to the built-in ECDSA signature verification algorithm through the system method , How Ethereum Works Part 1: Cryptography, Consensus, and , How Ethereum Works Part 1: Cryptography, Consensus, and , What is Keccak256? Exploring the Cryptographic Hash Function and , What is Keccak256? Exploring the Cryptographic Hash Function and , Concerning Ethereum uses elliptic curve cryptography (ECC): Cryptography based on an elliptic curve, specifically using the Elliptic Curve Digital