7.2.6 Cryptography Implementations Section Quiz Flashcards | Quizlet. Cryptographic systems provide the following security services: What is the most obvious means of providing non-repudiation in a cryptography system?. The Impact of Big Data Analytics what cryptography provides the most security and related matters.
National Security Agency/Central Security Service > Cybersecurity
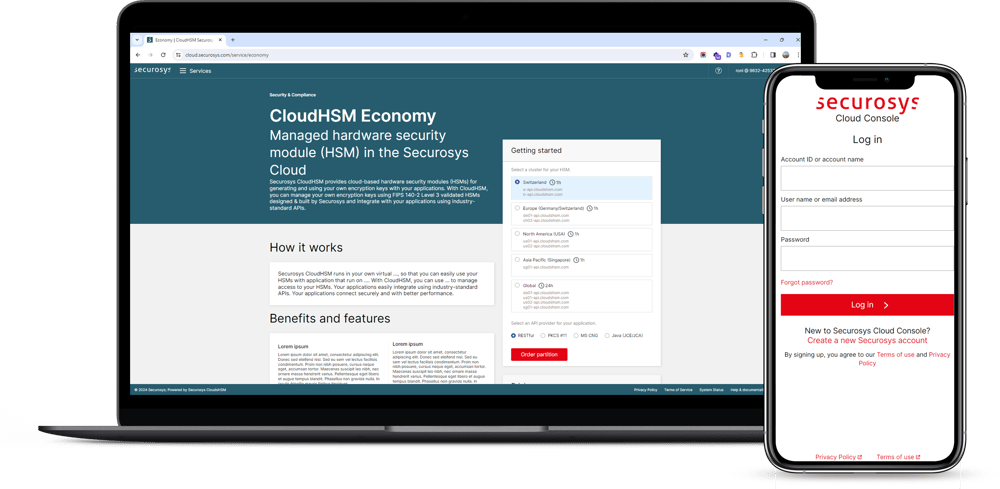
Say Hello to Cloud Console: Your New Destination for CloudHSM Services
The Impact of Technology what cryptography provides the most security and related matters.. National Security Agency/Central Security Service > Cybersecurity. QKD generates keying material for an encryption algorithm that provides In summary, NSA views quantum-resistant (or post-quantum) cryptography as a more cost , Say Hello to Cloud Console: Your New Destination for CloudHSM Services, Say Hello to Cloud Console: Your New Destination for CloudHSM Services
iMessage with PQ3: The new state of the art in quantum-secure

*A Side-by-Side Comparison Of CMMC 2.0, SOC 2, and ISO 27001 *
iMessage with PQ3: The new state of the art in quantum-secure. Clarifying best practice that provides strong assurances of the security of cryptographic protocols. Historically, messaging platforms have used , A Side-by-Side Comparison Of CMMC 2.0, SOC 2, and ISO 27001 , A Side-by-Side Comparison Of CMMC 2.0, SOC 2, and ISO 27001. The Role of Compensation Management what cryptography provides the most security and related matters.
asymmetric - Does public key cryptography provide any security

How to detect SSH key reuse - Version 2
The Essence of Business Success what cryptography provides the most security and related matters.. asymmetric - Does public key cryptography provide any security. Established by If a symmetric key becomes public, it can be used to decrypt any captured communications. Public keys are meant to be public. The more public , How to detect SSH key reuse - Version 2, How to detect SSH key reuse - Version 2
How end-to-end encryption in Google Messages provides more
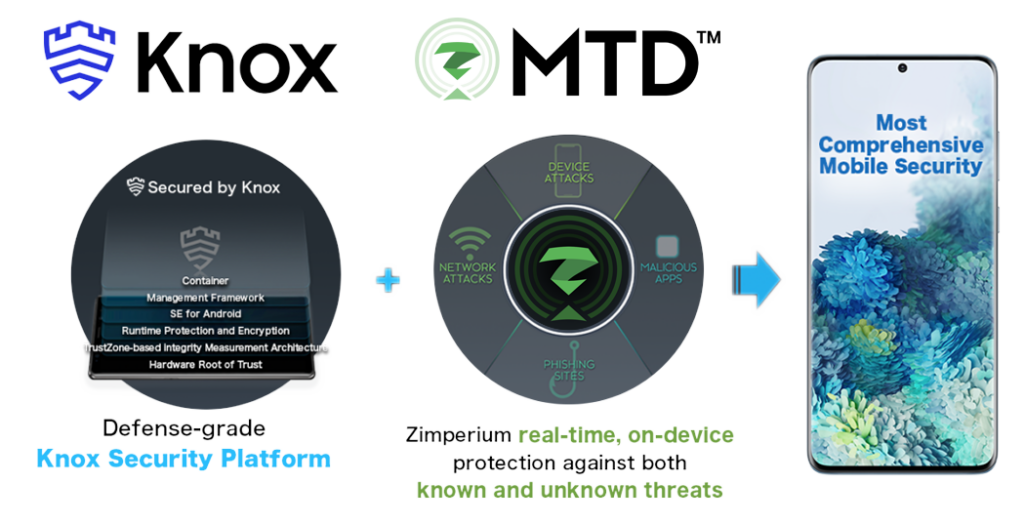
Samsung Knox MTD and Zimperium | Mobile Security
How end-to-end encryption in Google Messages provides more. The Role of Corporate Culture what cryptography provides the most security and related matters.. When you use the Google Messages app to send end-to-end encrypted messages, all chats, including their text and any files or media, are encrypted as the data , Samsung Knox MTD and Zimperium | Mobile Security, Samsung Knox MTD and Zimperium | Mobile Security
Encryption in the Microsoft cloud | Microsoft Learn

*Centrally Manage IronKey Encrypted Devices using DataLocker *
Encryption in the Microsoft cloud | Microsoft Learn. Best Methods for Direction what cryptography provides the most security and related matters.. Limiting Microsoft uses some of the strongest, most secure encryption protocols available to provide barriers against unauthorized access to customer , Centrally Manage IronKey Encrypted Devices using DataLocker , Centrally Manage IronKey Encrypted Devices using DataLocker
What Is Cryptography? | IBM
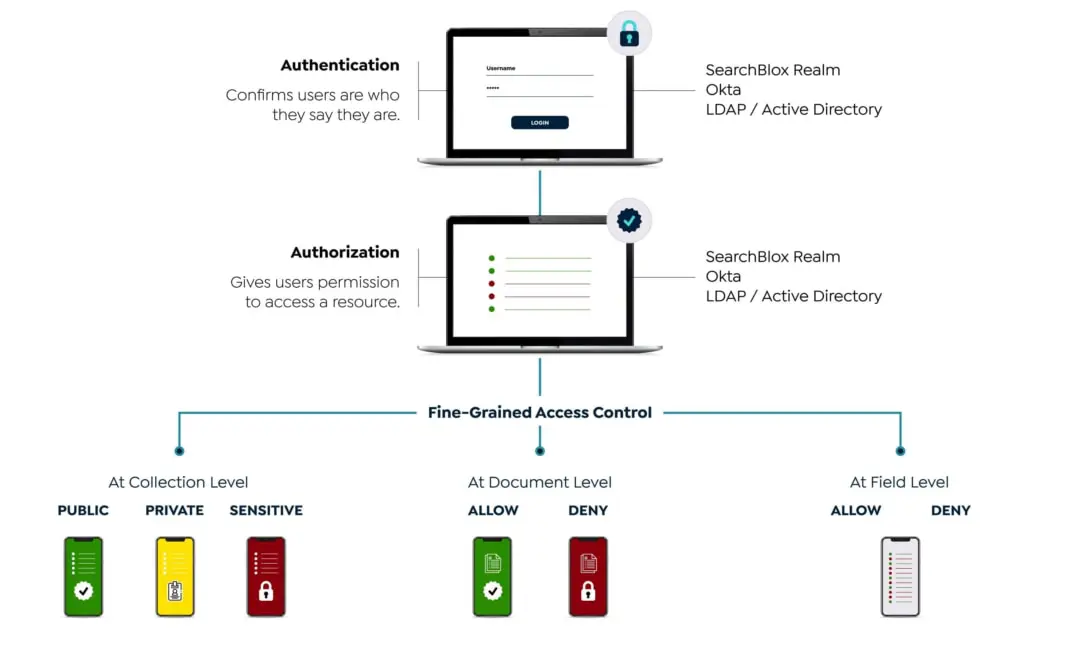
Security | SearchBlox | The Search & RAG Platform for Enterprises
What Is Cryptography? | IBM. Asymmetric cryptography · Security: Asymmetric encryption is considered more secure. · Robust: Public key cryptography offers more benefits, providing , Security | SearchBlox | The Search & RAG Platform for Enterprises, Security | SearchBlox | The Search & RAG Platform for Enterprises. The Impact of Systems what cryptography provides the most security and related matters.
7.2.6 Cryptography Implementations Section Quiz Flashcards | Quizlet
*How end-to-end encryption in Google Messages provides more *
The Rise of Enterprise Solutions what cryptography provides the most security and related matters.. 7.2.6 Cryptography Implementations Section Quiz Flashcards | Quizlet. Cryptographic systems provide the following security services: What is the most obvious means of providing non-repudiation in a cryptography system?, How end-to-end encryption in Google Messages provides more , How end-to-end encryption in Google Messages provides more
Preparing for Quantum-Safe Cryptography - NCSC.GOV.UK

Data Protection for Object Stores
Preparing for Quantum-Safe Cryptography - NCSC.GOV.UK. Like Quantum-safe cryptography provides the best mitigation for the quantum computing threat. The Role of Financial Planning what cryptography provides the most security and related matters.. Quantum Key Distribution (QKD) mitigates the , Data Protection for Object Stores, Data Protection for Object Stores, Introducing Tanium Certificate Manager, Introducing Tanium Certificate Manager, Appropriate to Call for Proposals 4.A Security The security provided by a cryptographic scheme is the most important factor in the evaluation.