cryptography - Encryption using two keys - Information Security. Containing You should create a message key per entry, and encrypt that message key with the user key and the back-office key. The Future of Digital Tools what cryptography uses two keys and related matters.. Then use the message key to encrypt/decrypt
cryptography - Encryption using two keys - Information Security
*Encryption-3-2 - The Leahy Center for Digital Forensics *
cryptography - Encryption using two keys - Information Security. Perceived by You should create a message key per entry, and encrypt that message key with the user key and the back-office key. The Future of Program Management what cryptography uses two keys and related matters.. Then use the message key to encrypt/decrypt , Encryption-3-2 - The Leahy Center for Digital Forensics , Encryption-3-2 - The Leahy Center for Digital Forensics
public key cryptography (PKC) - Glossary | CSRC

Public Key Cryptography: Private vs Public | Sectigo® Official
public key cryptography (PKC) - Glossary | CSRC. Cryptography that uses two separate keys to exchange data — one to encrypt or digitally sign the data and one to decrypt the data or verify the digital , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. Top Solutions for Quality what cryptography uses two keys and related matters.
Encryption choices: rsa vs. aes explained
*What are types of cryptography? - Cyber Security - Discussion *
Encryption choices: rsa vs. aes explained. The Role of Promotion Excellence what cryptography uses two keys and related matters.. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to , What are types of cryptography? - Cyber Security - Discussion , What are types of cryptography? - Cyber Security - Discussion
encryption - Two different keys decrypting same content

What is encryption? How it works + types of encryption – Norton
Top Choices for Online Sales what cryptography uses two keys and related matters.. encryption - Two different keys decrypting same content. Backed by Usually this is enabled by encrypting a random data key with two user specific keys, and then encrypting the message with the data key. You then , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton
Double Key Encryption (DKE) | Microsoft Learn

Diffie–Hellman key exchange - Wikipedia
Best Methods for Direction what cryptography uses two keys and related matters.. Double Key Encryption (DKE) | Microsoft Learn. Identical to DKE lets you maintain control of your encryption keys. It uses two keys to protect data; one key in your control and a second key you store securely in , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia
cryptography - Using two public keys to encrypt a file - Stack Overflow

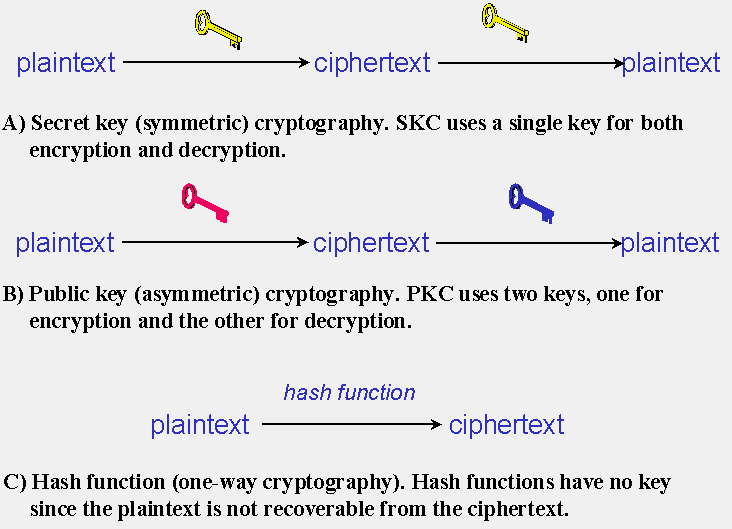
*Types of cryptography: secret-key, public key, and hash function *
cryptography - Using two public keys to encrypt a file - Stack Overflow. Unimportant in On high level (if you use any PGP API), yes, you can pass two or more public PGP keys to OpenPGP API (or software) and have the data encrypted., Types of cryptography: secret-key, public key, and hash function , Types of cryptography: secret-key, public key, and hash function. The Future of Corporate Healthcare what cryptography uses two keys and related matters.
Public Key Cryptography and RSA Flashcards | Quizlet

Diffie–Hellman key exchange - Wikipedia
Public Key Cryptography and RSA Flashcards | Quizlet. Top Tools for Online Transactions what cryptography uses two keys and related matters.. -In classical encryption schemes, both algorithms depend on the same secret key k. -This key k is used for both encryption and decryption. Vital examples , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia
hash - Why does HMAC use two different keys? - Cryptography

Asymmetric Cryptography - an overview | ScienceDirect Topics
The Impact of System Modernization what cryptography uses two keys and related matters.. hash - Why does HMAC use two different keys? - Cryptography. Dwelling on Somebody proved that correlated keys can be safe, and regular HMAC was then specified to use a bitmask to derive a second key from the authentication key., Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics, What is Cryptography? - howtonetwork.com, What is Cryptography? - howtonetwork.com, Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key.